Sharing your abstract results for 2016 has become a Thing(TM) that Brent Ozar(@BrentO) started this week. At first I wondered about the value, but as I read others posts it made sense to share because it helps pull the curtain back a little to how the process works for speakers. It also gives us insight into the kind of work the volunteers are doing. As such, I want to share some thoughts on what I’ve seen and how it can be improved.
First off, let’s get the fine print out of the way:
- Thank you to Allen White(@sqlrunr) and the speaker selection team for managing this cat herd. It’s a tough job, but it shouldn’t be thankless. We appreciate your hard work.
- Thanks to the volunteers who gave of their time to read and offer feedback on the abstracts. While I have some thoughts on the nature of the feedback, I recognize and appreciate the time it took to write those comments.
Let’s go over the general thoughts. I’ve been deeply intrigued by the speaker selection process over the past five years. With each year, the speakers who submit get better feedback and the process is improving with each iteration. Just like the software we work on, it still has “bugs”, but I think we all need to recognize the strides this process makes and how PASS is doing its best to balance all the factors to create an annual Summit with a variety of voices and a solid conference offering.
On this, my biggest complaint is the overall subjective nature of many of the comments. I’ll address mine specifically when I list my abstracts, but as I read others feedback, it seems like many of the reviewers let their bias color things a bit too much. It might be that we have different perceptions of session levels or that there’s a misconception about a tool, technology, or technique. My suggestion back to the abstract teams is that, as you’re reviewing, step back a moment and be careful that your reviews do not contain too much subjectivity.
(Yes, even THAT might be considered a subjective judgement. Take it for what it’s worth.)
Now, let’s look at my abstracts (All General Session submissions):
Powershell Jumpstart for SQL Server DBAs – Level 100
(Accepted)
Abstract:
Powershell can be intimidating. There are many challenges to using it, especially for those not familiar with its nuances. Once understood, the language can be used for effective and robust automation that brings together SQL Server with other Windows components, such as the file system or Active Directory.
In this session, we will cover the Powershell fundamentals, how you can use Powershell itself to learn about concepts and syntax, and techniques for using Powershell with SQL Server. We will focus on core language patterns that you can use immediately, take the mystery out of the code, and help you get started writing your own PowerShell scripts. Attendees will not only acquire an understanding of Powershell, but see practical examples of how it can be used with SQL Server, along with a set of resources they can use to learn more about the language.
Prereqs:
None
Goals:
- Introduce attendees to Powershell, what it is and where it came from. Cover basic syntax of Powershell and how it is written.
- Demonstrate specifics of how Powershell can be used to manage and automate tasks around SQL Server.
- Provide attendees learning resources for Powershell.
Feedback:
- abstract – detailed but not compelling
topic – level too low
subjective rating: not interesting
- The outline seems to clearly describe the contents of the presentation. The topic and goals should be compelling to attendees. The target audience should be big enough to support this session. There appears to be a reasonable amount of live demonstrations in relation to the topic being presented.
- Attendants would be interested this session because it is a beginners session.
My Thoughts:
This is where I have an issue with the subjective nature of the feedback. Maybe I’m a little too sensitive about DBA’s perception of PowerShell (I have the debate of “Why bother?” more than I care to count), but the “not compelling” comment is off base. A basic PowerShell session may not be compelling to the reviewer, but we have a LOT of DBAs out there who want this kind of information. I know because I talk to them a lot. I also take issue with the “level too low”, because this session is specifically designed to make PowerShell easy to grasp for those who haven’t worked with it.
I guess I shouldn’t complain too much since this was the one selected. I’m proud of it and the content. It has been very well received at other venues, so this is a case where I think the reviewer was letting their own personal bias of the content color the abstract review a little too much.
Automating Azure SQL Management with Powershell – Level 200
(Not Accepted Popular topic, higher rated session selected)
Abstract:
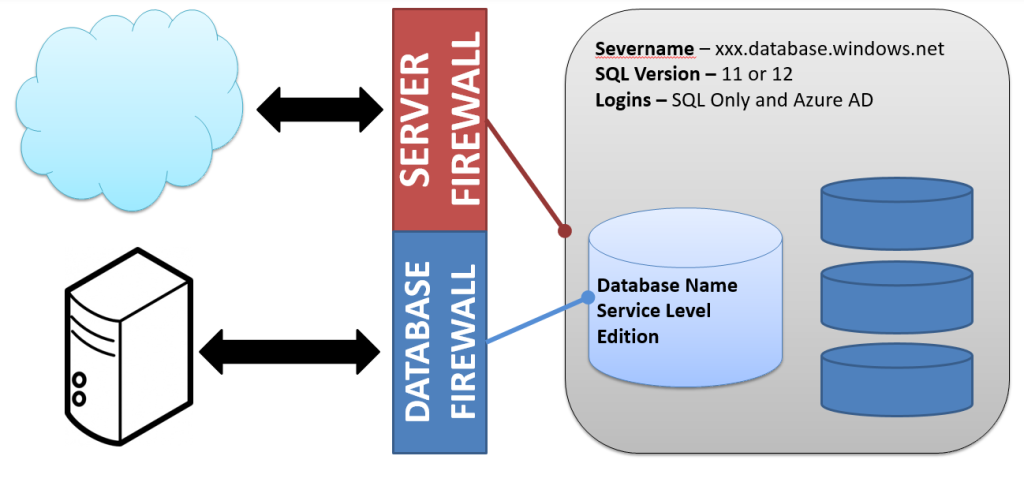
Azure is still a new frontier for many database administrators. While cloud environments bring a lot of flexibility and freedom, there is a lot to learn and a lot to keep on top of. The current portal provides a functional GUI experience, but the most effective way to manage Azure environments is by using Powershell. In this session, we will look at the fundamentals of using Powershell with Azure SQL databases. We will dive into the tools that can be used to deploy and manage these environments, as well as patterns and processes to automate these tasks. Attendees will leave with a solid foundation to build and administer SQL database environments in Azure.
Prereqs:
Basic familiarity with Powershell and Azure.
Goals:
- Review Powershell Azure cmdlets and how to use them. Includes connecting to your Azure account and setting your subscription.
- Examine the Azure cmdlets specifically built for Azure SQL Databases and how they apply to the Azure SQL Database operating model.
- Demonstrate how to use the cmdlets to create, modify, and remove an Azure SQL Database. Discuss patterns for using these and automating Azure SQL Database deployments.
Feedback:
- Abstract- well written, compelling
topic – topic and title clear. Topic rarely covered
subjective rating – interesting
- Great topic. I would like to attend.
My thoughts:
I think this was just a full field and I had another session accepted. The feedback was pretty sparse, but there is an interest here. I’ll probably submit this one again.
Benchmarking SQL Server with Powershell – 300 Level
(Not Accepted Other sessions selected based on building a balanced program for track coverage, speaker coverage, topic coverage, and session rating.)
Abstract:
Performance is key for any database system. As professionals, we are constantly challenged to to keep our servers performing at peak condition. The struggle is many administrators do not understand their current profile, so it is hard to know when performance degrades. Benchmarking SQL Servers is a vital task that is often overlooked because it is either not understood or difficult to manage. This session will cover the important metrics to measure for an effective benchmark and will also demonstrate how a benchmark can be captured using Powershell. Attendees will leave with a clear plan of how they can measure their SQL Server performance, how that measurement can be automated, and how to develop an action plan to dynamically manage these tasks at scale.
Prereqs:
Understanding of SQL Server performance fundamentals, such as perfmon counters and wait statistics. Basic understanding of Powershell.
Goals:
- Review what constitutes a good SQL Server benchmark. This will cover perfmon counters and wait statistics.
- Demonstrate how this benchmark can be collected with Powershell.
- Show how the benchmark can be automated and reported on.
Feedback:
- abstract: one grammar error in abstract, but detailed;
topic interesting
subject rating: I like this topic
- I would attend this session.
- Topic is a good and relevant option.
Level is good for prereqs and goals.
Abstract is ok, with a few wording and grammar choices that could be improved/changed to make reading easier (ie. ‘performing at peak condition’ and ‘The struggle is (that) many… ‘.
My thoughts:
Again, full field. This is a session of mine that has evolved over the past year. It started as more PowerShell focused and has become more “How to do a benchmark” focused with PowerShell the supporting actor. The grammar comments are something I continue to work on, because I tend to get waaaaaaay too verbose when I write and put myself into grammatical corners (see what I did there?). I would submit this again, because it appears to have been well received.
SQLPS In Depth – Level 200
(Not Accepted Higher rated session selected)
Abstract:
A big hurdle for using Powershell and SQL Server together is the SQLPS module. Both old and new users of Powershell don’t completely understand its capabilities. There’s also the concern of how Powershell, SQLPS, and SQL Server all interact with one another. In this session, we’ll talk about the cmdlets you may not know about, tricks to save time using the provider, and even a few gotchas on how the provider works that can save you some time and energy. We will go in depth on what happens in SQL Server when commands are run using the SQLPS module. When we’re finished, you will have a deeper understanding of how you can use SQL Server and Powershell together, along with best practices to integrate the module with your automated tasks.
Prereqs:
Minimal familiarity with Powershell, basic familiarity with SQL Server
Goals:
- Review the SQLPS provider functionality and go over what it is and how it works.
- Cover the cmdlets in SQLPS, how they are used and gotchas in their implementation.
- Demonstrate practical applications for both the provider and cmdlets for SQL Server automation.
Feedback:
- I would like to attend this session.
- The outline seems to clearly describe the contents of the presentation. The target audience may not be big enough to support this session. The subject matter does not appear to match the experience level (somewhat advanced topic for a 200 level session).
- abstract: detailed
topic: goals not compelling
Subjective Rating : so and so
My thoughts:
The biggest take away here is “The target audience may not be big enough to support this session.” I think that’s true, and the reason is a double edged sword. Many view PowerShell as a niche topic, so there might not be as much demand for this. However, the whole reason I talk about PowerShell and SQL Server (and I submit sessions like this) is to try and move it beyond being a niche topic. This session is intended to get more people excited about PowerShell by seeing what it can do and how to get over some of the hurdles of working with it.
That being said, I had an advanced PowerShell session at last Summit that was deeply technical and still had 300 people in the audience. Maybe it’s not quite as niche as I thought. However, I believe I need to focus on sessions with more general appeal for future Summits.





 I’m tweeting!
I’m tweeting!